2023. 3. 26. 20:30ㆍ정보보안/CTFLOG

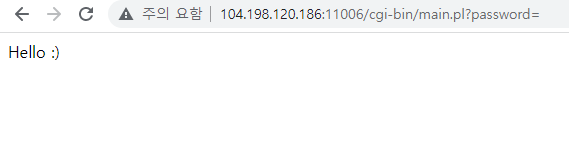
This challenge is written in perl.
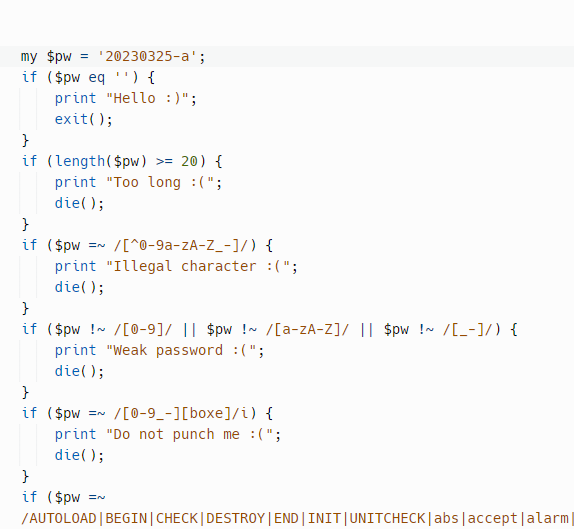
#!/usr/bin/perl
use strict;
use warnings;
use CGI;
use URI::Escape;
$SIG{__WARN__} = \&warn;
sub warn {
print("Hacker? :(");
exit(1);
}
my $q = CGI->new;
print "Content-Type: text/html\n\n";
my $pw = uri_unescape(scalar $q->param("password"));
if ($pw eq '') {
print "Hello :)";
exit();
}
if (length($pw) >= 20) {
print "Too long :(";
die();
}
if ($pw =~ /[^0-9a-zA-Z_-]/) {
print "Illegal character :(";
die();
}
if ($pw !~ /[0-9]/ || $pw !~ /[a-zA-Z]/ || $pw !~ /[_-]/) {
print "Weak password :(";
die();
}
if ($pw =~ /[0-9_-][boxe]/i) {
print "Do not punch me :(";
die();
}
if ($pw =~ /AUTOLOAD|BEGIN|CHECK|DESTROY|END|INIT|UNITCHECK|abs|accept|alarm|atan2|bind|binmode|bless|break|caller|chdir|chmod|chomp|chop|chown|chr|chroot|close|closedir|connect|cos|crypt|dbmclose|dbmopen|defined|delete|die|dump|each|endgrent|endhostent|endnetent|endprotoent|endpwent|endservent|eof|eval|exec|exists|exit|fcntl|fileno|flock|fork|format|formline|getc|getgrent|getgrgid|getgrnam|gethostbyaddr|gethostbyname|gethostent|getlogin|getnetbyaddr|getnetbyname|getnetent|getpeername|getpgrp|getppid|getpriority|getprotobyname|getprotobynumber|getprotoent|getpwent|getpwnam|getpwuid|getservbyname|getservbyport|getservent|getsockname|getsockopt|glob|gmtime|goto|grep|hex|index|int|ioctl|join|keys|kill|last|lc|lcfirst|length|link|listen|local|localtime|log|lstat|map|mkdir|msgctl|msgget|msgrcv|msgsnd|my|next|not|oct|open|opendir|ord|our|pack|pipe|pop|pos|print|printf|prototype|push|quotemeta|rand|read|readdir|readline|readlink|readpipe|recv|redo|ref|rename|require|reset|return|reverse|rewinddir|rindex|rmdir|say|scalar|seek|seekdir|select|semctl|semget|semop|send|setgrent|sethostent|setnetent|setpgrp|setpriority|setprotoent|setpwent|setservent|setsockopt|shift|shmctl|shmget|shmread|shmwrite|shutdown|sin|sleep|socket|socketpair|sort|splice|split|sprintf|sqrt|srand|stat|state|study|substr|symlink|syscall|sysopen|sysread|sysseek|system|syswrite|tell|telldir|tie|tied|time|times|truncate|uc|ucfirst|umask|undef|unlink|unpack|unshift|untie|use|utime|values|vec|wait|waitpid|wantarray|warn|write/) {
print "I know eval injection :(";
die();
}
if ($pw =~ /[Mx. squ1ffy]/i) {
print "You may have had one too many Old Pal :(";
die();
}
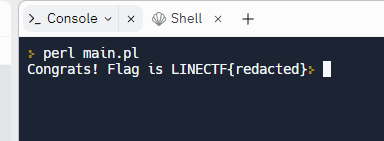
if (eval("$pw == 20230325")) {
print "Congrats! Flag is LINECTF{redacted}"
} else {
print "wrong password :(";
die();
};In this code, you can find a lot of filter and checking your param if valid.
The conditions for this challenge are as follows:
1. nothing in param, print hello :)
2. param len is bigger than 20 print Too long..
3. if you put in param [0-9a-zA-Z-_ ] else print Iliger char
4. if you don't put the any of [0-9a-zA-Z-_ ] print weak password..
5. if param has any of [boxe] print Do not punch me :(
6. if param has function of perl, print I know eval injection.
7. if param has any of [Mx. squ1ffy] print you may have had one too many Old Pal :(
8. if password is 20230325 print Flag
so, you have to satisfied this conditions.
but, it is not easy to solve.
I saw the condition that it could not exceed 20 digits and said that it could be solved through brute force.
this is impossible In the meantime,
I learned about the existence of a function that interprets
the perl function as a number within the eval function.
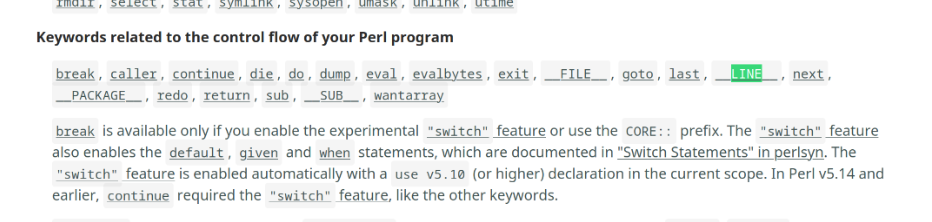
20230326-__LINE__
__LINE__
has value of '1' in execute func
so, 20230326-1 == 20230325

Note that strict is being used in this chall.
All undeclared variables are warned, and Hacker? phrase will appear.
Therefore, true processing such as 20230325-a is impossible. (Available when strict is not present)
'정보보안 > CTFLOG' 카테고리의 다른 글
| [CTF] DEFCON31 Quals (0) | 2023.05.29 |
|---|---|
| [CTF] GreyCTF'23 write up (0) | 2023.05.22 |
| [CTF] LINE CTF 2023 - baby simple go url (0) | 2023.03.26 |
| [CTF] B01ler_ctf - voidciphr (0) | 2023.03.20 |
| [CTF] LOGCON - warmup (0) | 2023.01.17 |